Executive Foreword
Ransomware is just a cybersecurity issue. It’s a financial leadership stress test.
The decisions made in the first 24 hours of an attack determine how quickly an organization can restore operations, protect liquidity, and preserve confidence.
This framework reflects the lessons we’ve learned by looking at resilience through a financial lens. It’s built for CFOs who understand that preparation means planning for continuity – and making sure your business can keep moving through the disruption.
– Greg Guelcher, Chief Financial Officer, Coretelligent
Move 1 | Map Risk in Dollars
You can’t manage what you haven’t monetized. Listing every critical system, vendor, and revenue dependency reveals which failures hurt first – and most.
| Function | Example Impact per Day | Key Dependency |
| Billing & AR | $2.5M | Cloud ERP availability |
| Payroll | $450K | HRIS + banking APIs |
| Procurement | $1.1M | Supplier portals |
Document these exposures in your risk register and forecast models. Treat downtime like any other cost driver with measurable impact.
If you can’t express a system in dollars, it won’t get prioritized when hours matter.
Move 2 | Build a Cyber Reserve
Recovery draws cash before insurance reimburses it. A dedicated reserve keeps operations solvent when expenses spike and receivables pause.
How to Approach It
- Set aside 1–2% of OpEx as a reserve.
- Model a seven- to 10-day outage scenario.
- Review annually as coverage limits and deductibles shift.
Position the reserve within your liquidity strategy to ensure predictable access to recovery capital.
Think of it as bridge financing for resilience – the capital you’ll need before the claims adjuster calls back.
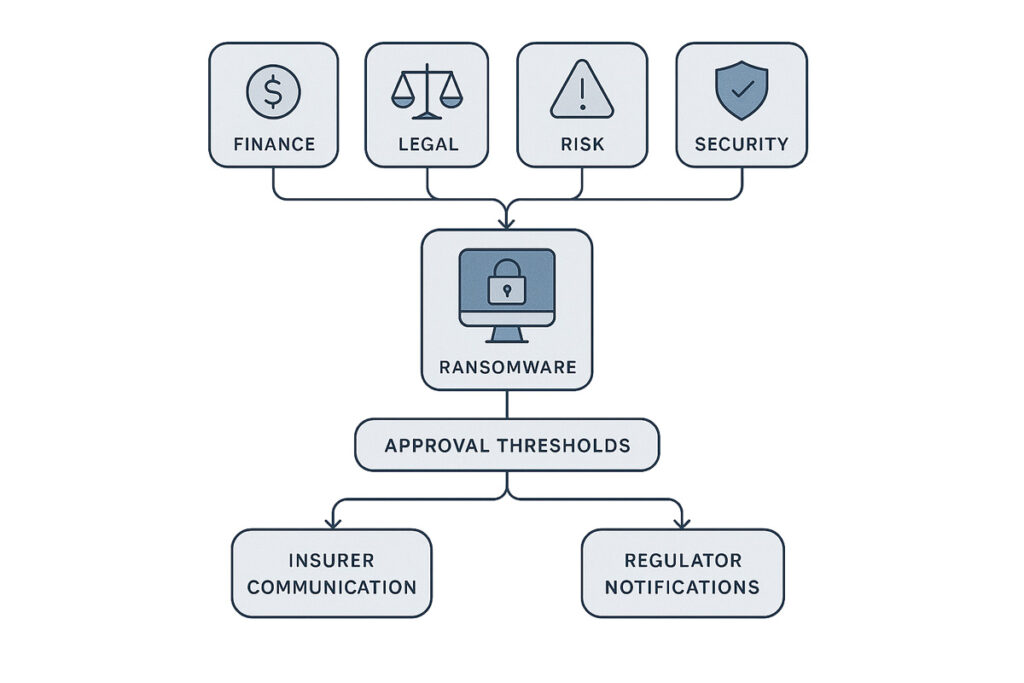
Move 3 | Establish a Ransom Decision Strategy
Ransom payments are financial, legal, and reputational events rolled into one. Waiting until an attack to decide policy adds delay and cost.
How to Approach It
- Convene Finance, Legal, Risk, and Security to define thresholds for consideration.
- Identify who authorizes payments, who liaises with insurers, and who communicates with regulators.
- Record the framework in the incident-response plan and board materials.
Ensure your ransom strategy aligns with governance and compliance obligations before a crisis forces the question.
Clear decision rights reduce recovery time more than any negotiation tactic ever will.
Move 4 | Audit Recovery Readiness
Response speed depends on how well Finance and Operations function without digital systems. Practicing manual continuity exposes choke points before real money is at risk.
How to Approach It
- Participate in at least two cross-functional simulations per year.
- Time how long it takes to approve emergency spend, process payroll manually, and shift procurement to contingency vendors.
- Record gaps and assign owners for remediation.
Use tabletop results to adjust liquidity buffers and authorization workflows.
Every dry run buys minutes in a real event – and minutes compound into millions.
Move 5 | Align Recovery Targets with Risk Appetite
Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) translate directly into revenue at risk. Targets must reflect what the business can truly afford to lose.
How to Approach It
- Partner with IT to quantify the daily cost of downtime per system.
- Map those costs against current RTO/RPO values.
- Adjust investment to close the gap where impact exceeds tolerance.
Include recovery-objective review in annual planning and capital budgeting cycles.
Budgeting for downtime is cheaper than explaining why unbudgeted downtime occurred.
Move 6 | Harden and Automate Backups
Your backups are your last line of defense – and your first line of recovery. But only if they’re clean, accessible, and tested.
How to Approach It
- Keep backups offline or in immutable storage.
- Automate testing and verification to confirm restoration speed.
- Review recovery procedures regularly with both IT and Finance.
Make backup verification part of your financial risk audits. The faster you can restore, the faster revenue resumes.
A clean, tested backup is the fastest route back to cash flow.

Move 7 | Institutionalize Governance Reporting
Boards and regulators increasingly expect visibility into resilience. Integrating ransomware metrics into quarterly reporting proves readiness and accelerates decision-making when pressure mounts.
How to Approach It
- Include recovery KPIs – containment time, insured exposure, and financial variance – in Finance and Audit updates.
- Track post-incident improvements as part of your governance cadence.
Own resilience reporting the same way you own liquidity and compliance dashboards.
Transparency shortens board debates and strengthens confidence before the next incident tests it.
Closing Thought
These seven moves turn ransomware planning into measurable, repeatable practice – so when disruption comes, Finance is already one step ahead of the clock.
About Coretelligent
We provide industry-specific managed IT support, cybersecurity and governance services, and AI transformation solutions that lead to better, faster business outcomes.
As a strategic partner, we protect your operations, data, and reputation – so you can grow and innovate without having to worry about your technology.
Learn more at coretelligent.com
From governance design to backup hardening to liquidity stress testing, our cyber and IT leadership teams help CFOs operationalize resilience in a measurable, repeatable way. Speak with a Coretelligent resilience strategist. today.
