The NIST Cybersecurity Framework (CSF) is a comprehensive set of guidelines and best practices aimed at helping organizations effectively manage and prioritize their cybersecurity efforts.
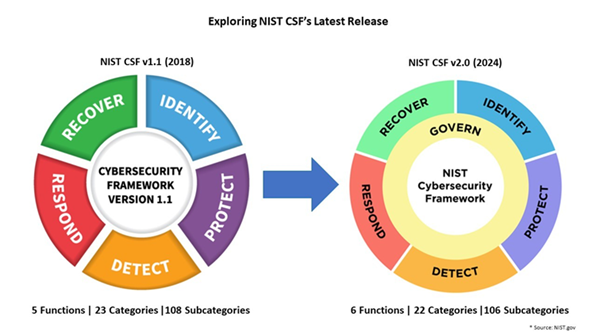
With the release of version 2.0, a new core function, Govern, has been added, enhancing the existing functions: Identify, Protect, Detect, Respond, and Recover. These six core functions now provide a strategic, high-level overview of the lifecycle for managing cybersecurity risk.
History and Background
The National Institute of Standards and Technology (NIST), established in 1901, has played a pivotal role in setting standards across various domains. A common misconception among clients is their reference to “NIST compliance,” not realizing that NIST isn’t a single standard but a comprehensive entity that sets various guidelines.
Key milestones in NIST’s cybersecurity focus include:
- Early 2000s: Focus on cybersecurity compliance began.
- 2002: Federal Information Security Management Act (FISMA).
- 2010: Controlled Unclassified Information (CUI) Executive Order.
- 2015: Release of NIST SP 800-171 guidelines.
In response to Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” the NIST Cybersecurity Framework (CSF) was developed in 2013. The latest version, CSF 2.0, is designed to be universally applicable, catering to businesses of all sizes and sectors.
Is This Just Another Framework?
The CSF integrates and aligns with various existing cybersecurity standards, guidelines, and best practices, allowing organizations to build on their current cybersecurity programs. Unlike prescriptive frameworks like the CIS Critical Security Controls, the CSF provides a flexible structure for understanding and managing cybersecurity risks.
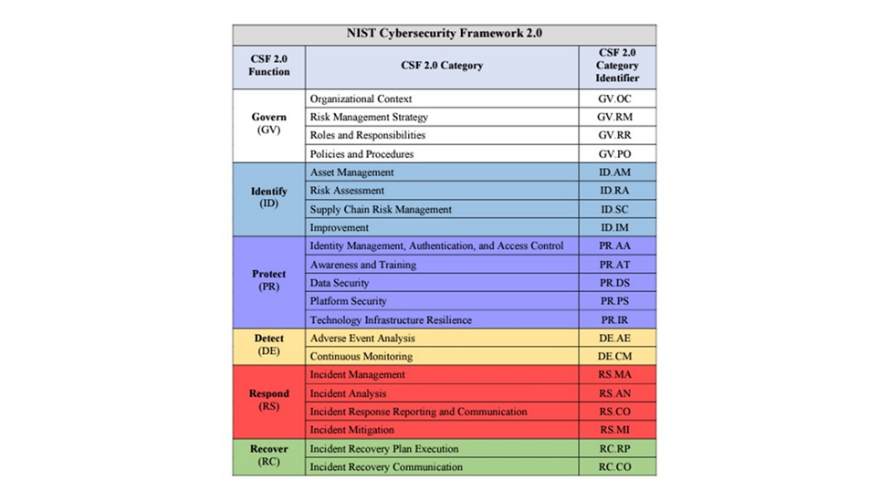
Key features of CSF 2.0 include:
- Informative References: These references serve as connections between the CSF and other cybersecurity frameworks, standards, guidelines, and resources. They help organizations understand how the CSF relates to other cybersecurity initiatives and facilitate the integration of the CSF with existing practices. Learn more ->
- Maturity Model: The CSF 2.0 includes implementation tiers (Partial, Risk Informed, Repeatable, Adaptive) that help organizations assess their cybersecurity maturity. This model allows businesses to identify their current state of cybersecurity and set realistic goals for improvement.
- Organizational Profiles: CSF 2.0 provides guidance on creating detailed organizational profiles. These profiles help tailor the framework to an organization’s specific needs and circumstances, ensuring that cybersecurity efforts are aligned with the organization’s goals and risk environment.
- Incident Response Guidance: The updated framework includes detailed guidance on incident response planning and execution. This helps organizations develop robust response strategies to handle cybersecurity incidents effectively, minimizing potential damage and facilitating quick recovery. Learn more ->
How Does It Compare to Other Frameworks?
While frameworks like the CIS Critical Security Controls offer prescriptive measures, the CSF 2.0 provides a common language and structure for understanding and managing cybersecurity risks. Unlike CIS, which prescribes specific technical controls, CSF 2.0 offers a more flexible and strategic approach.
Examples of CIS Critical Security Controls v8 vs. CSF 2.0 Controls:
CIS Control 1: Inventory and Control of Enterprise Assets vs. CSF Identify Function: requiring organizations to maintain detailed inventories of hardware devices. This control goes in depth about what information to collect about each asset, what type of tools could be used, and how often to update the inventory.
In contrast, the CSF’s Identify function takes a broader approach, encouraging organizations to understand and manage their assets and resources, including hardware, software, and data, within the context of their overall risk management strategy.
Cyber Defense Matrix:
Additionally, Tools like the Cyber Defense Matrix further illustrate the relationship between different frameworks and can help organizations understand how the CSF fits into their overall cybersecurity strategy.
For those unfamiliar, the Cyber Defense Matrix, developed by Sounil Yu, is a tool that helps organizations understand and map their cybersecurity capabilities across different stages of the attack lifecycle and various operational domains. It categorizes capabilities into five functions: Identify, Protect, Detect, Respond, and Recover, similar to the NIST CSF.
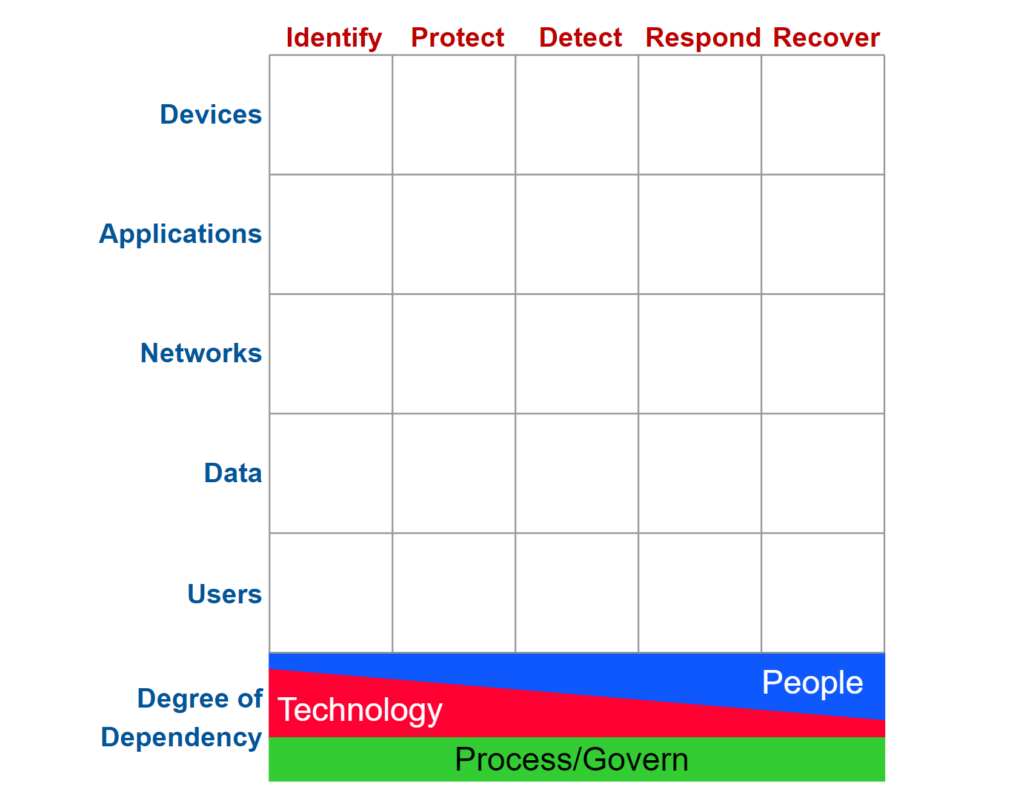
- Mapping Capabilities: The matrix provides a visual representation of how different security controls and solutions align with the CSF functions, helping organizations identify gaps and overlaps in their cybersecurity strategies.
- Strategic Planning: By using the matrix, organizations can better strategize their cybersecurity investments and ensure comprehensive coverage across all necessary functions and domains. It aids in integrating various frameworks and standards, including CIS controls and CSF, providing a holistic view of an organization’s security posture.
The Cyber Defense Matrix enhances the practical application of the CSF by offering a structured way to align security controls with organizational objectives, making it easier for businesses to understand their cybersecurity landscape and improve their defenses effectively.
How Can NIST CSF v2 Help Your Business?
Cybersecurity is a critical business risk that must be considered in all decision-making processes. The NIST CSF helps organizations of all sizes identify and manage cyber risks effectively.
Key benefits to know:
- Continuous Improvement: Ensures new assets and threats are continually assessed.
- Prompt Responses: Enables swift action to minimize impact.
- Wide Acceptance: Recognized and respected globally.
By adopting the CSF, organizations can enhance their resilience against cyber threats and align their cybersecurity efforts with best practices recognized globally.
Takeaways
The NIST Cybersecurity Framework 2.0 offers a robust, adaptable approach to managing cybersecurity risks.
Its comprehensive structure and flexibility make it an essential tool for any organization looking to improve its cybersecurity defenses and navigate the complexities of today’s cyber threat landscape.