RIA Cybersecurity: Prepare for New SEC Cybersecurity Requirements
The SEC’s new cybersecurity requirements for registered investment advisers (RIAs) will soon mandate firms to develop robust policies, report incidents, and disclose risks in their marketing materials. To prepare, RIAs should implement comprehensive cybersecurity policies, conduct risk assessments, establish clear disclosure procedures, ensure continuity planning, and maintain thorough documentation to comply with the upcoming regulations and enhance their cybersecurity posture.
Breach Detection: Could You Detect a Data Breach?
Detecting data breaches early is crucial for limiting damage, preserving reputation, and preventing further unauthorized access. Many businesses struggle with real-time breach detection, but by prioritizing active monitoring, identifying high-value data, and implementing rapid remediation strategies, they can better protect their sensitive information and mitigate the impact of breaches.
CPRA Vs CCPA? Ready for the July 2023 Deadline?
The California Privacy Rights Act (CPRA) strengthens and expands the consumer privacy protections of the CCPA. On July 1, 2023, new requirements were implemented. Explore the key differences in the update requirements for protecting sensitive personal information, conducting security audits, and ensuring third-party vendor security, making it crucial for businesses to stay updated and work with knowledgeable IT partners to navigate these regulations.
What is Cyber Hygiene & Why is it Important? (Best Practices)
Cyber hygiene involves the consistent implementation of cybersecurity best practices to secure networks and critical data. Key practices include enabling multi-factor authentication, using strong and unique passwords, keeping software updated, recognizing phishing and social engineering tactics, protecting mobile devices, and using VPNs for secure remote access.
The Importance of Data Loss Prevention
Data loss prevention (DLP) involves implementing systems, policies, and training to protect sensitive information from being misused, lost, or accessed by unauthorized users. Businesses can reduce the risk of data loss by developing comprehensive security policies, conducting regular vulnerability assessments, implementing access controls, and ensuring proper data backup and disaster recovery plans.
How to Effectively Assess Enterprise Backup Solutions?

Disasters and cyber-attacks happen, but data loss does not have to be inevitable. Data loss can be avoided or mitigated with a robust backup and disaster recovery solution (BDR). Surviving a catastrophic data loss event depends on choosing the right BDR solution. But you need to understand the critical components in order to successfully evaluate […]
Are You Getting the Most Out of Your Data Governance Program?
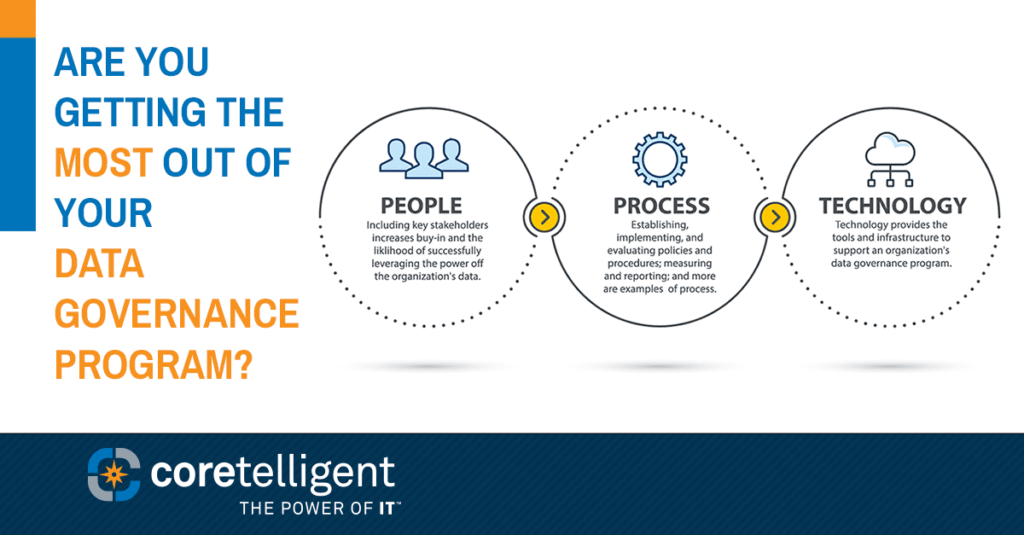
Last month we shared the first in our series about the importance of having a data governance program. With this post, we go more in-depth about why data governance is the key to unlocking the power of your data to drive growth and avoid risk. What is a Data Governance Program? Data is the new […]