AI Governance Blueprint for the C-Suite
Secure Adoption of Microsoft Copilot for Executives Effective AI governance is crucial for executives in regulated industries. This blueprint outlines best practices for protecting data and managing regulatory requirements while governing Microsoft 365 Copilot strategically, encompassing stakeholder roles, risk assessments, and compliance frameworks. Download the road map. Get The Road Map Now
Top 5 Questions Every C-Suite Should Ask About Microsoft Copilot
Top 5 Strategic Questions for Copilot Adoption Before deploying Microsoft 365 Copilot, executives must ask the right strategic questions. This concise guide is designed for mid-market leaders to gain clear insights on balancing innovation with governance and confidently leverage Microsoft Copilot. Download the white paper. Get The Whitepaper Now
Executive Playbook for Secure Microsoft Copilot Productivity

Maximizing Strategic Productivity with Microsoft Copilot AI-powered productivity offers significant advantages, but realizing them requires thoughtful planning and governance. This whitepaper discusses how Microsoft 365 Copilot, when paired with Microsoft Purview, enhances productivity while maintaining security. Download the white paper. Get The Whitepaper Now
CFO’s Guide: Managing Financial and Cyber Risk with Microsoft Copilot
Navigating Financial and Cyber Risks with Copilot For CFOs, AI tools like Microsoft 365 Copilot deliver exceptional productivity gains, but financial and cyber risks must be carefully managed. This guide provides practical steps for safely deploying Copilot within your organization. Download the CFO guide. Get The Guide Now
Navigating Compliance and Governance Risks from AI-Phishing

Stay Ahead of Compliance Gaps Triggered by AI-Phishing AI-enhanced phishing breaches are triggering HIPAA, SOX, PCI, and CCPA violations across industries. This guide equips CISOs and COOs to strengthen governance programs, mitigate breach fallout, and meet the increasing expectations of regulators, boards, and clients. Download the compliance guide. Get The Guide Now
Navigating AI-Driven Phishing Threats: Essential Insights for Executives

Executive Insights on Defending Against AI-Driven Threats Phishing threats powered by AI are growing more targeted and costly. This executive brief delivers the strategic highlights every C-level leader needs to understand the risks, reinforce defenses, and empower teams to detect and disrupt attacks before damage occurs. Download the executive brief. Get The Brief Now
Managing Cyber Financial Risk: A CFO’s Guide to AI Phishing and BEC
CFO Playbook: Quantify and Control Cyber Financial Risk BEC scams and phishing breaches pose direct financial threats to mid-sized businesses. This guide gives CFOs the tools to quantify risk, optimize cybersecurity investments, and safeguard liquidity and reporting integrity in an age of intelligent cybercrime. Download the guide. Get The Guide Now
How CIOs and CTOs Can Defend Against AI-Powered Phishing

Protect Digital Strategy from AI-Powered Threats Phishing attacks now threaten infrastructure, data, and continuity across transformation projects. This technical brief helps CIOs and CTOs embed scalable cybersecurity practices that accelerate innovation—without compromising uptime or integrity. Download the technical brief. Get The Brief Now
AI-Powered Phishing and BEC: Roadmap for Executive Risk Management

Combat AI-Powered Phishing with an Executive-Ready Playbook AI-enhanced phishing and BEC attacks are rapidly evolving—demanding a coordinated, executive-level response. This roadmap outlines how to align cybersecurity, compliance, and business continuity with risk mitigation strategies that reduce exposure, prevent fraud, and protect the enterprise. Download the white paper. Get The Whitepaper Now
The True Cost of Siloed Cybersecurity
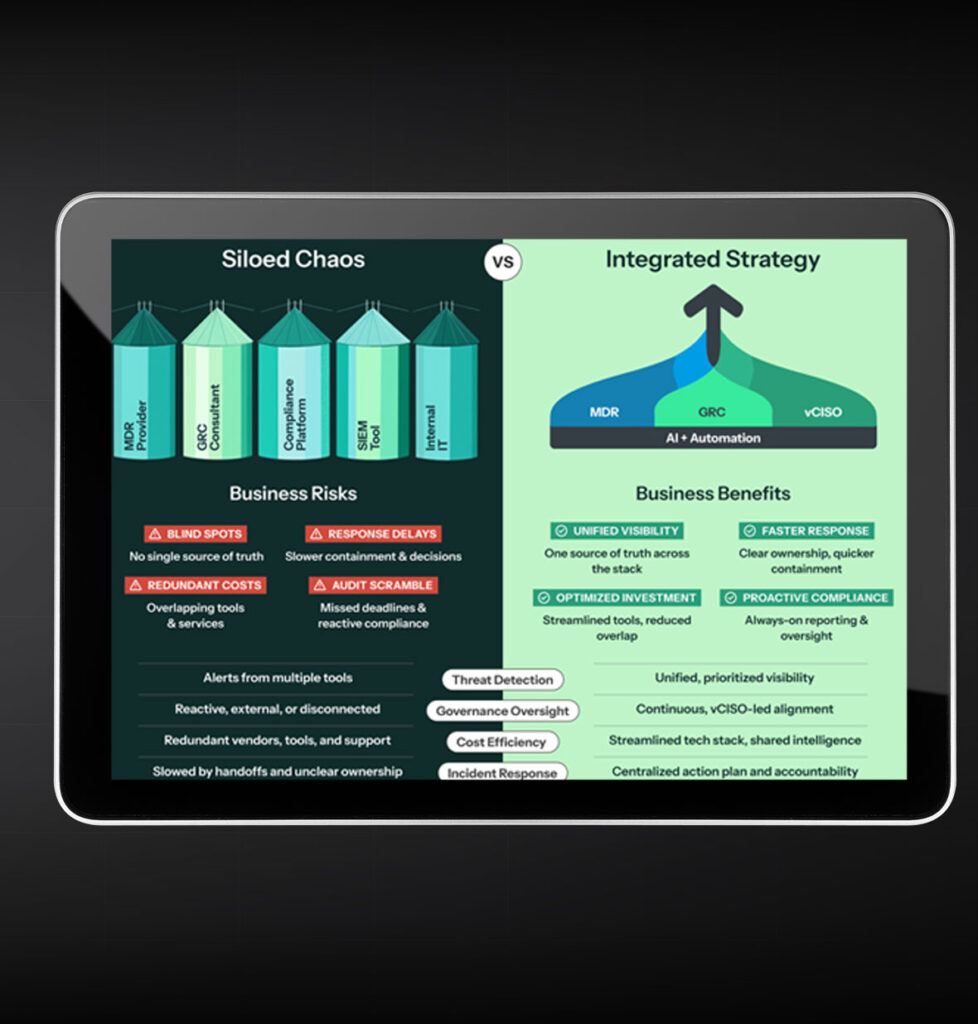
Who Owns the Risk in Your Cybersecurity Stack? Siloed cybersecurity solutions cause blind spots, redundant costs, and delayed response times. Discover the real costs of fragmented security—and how an integrated strategy reduces risk and enhances business resilience. Download the infographic. Get The Infographic Now